
Hackers are always looking for an opportunity to attack a company's devices and network. According to research, over 2,200 cyber-attacks happen daily, translating to one...
For hackers, American small business culture represents a target-rich environment. Small businesses don’t often possess robust protocols in place to deter attackers. They might not use commercial-grade antivirus, and may not consistently employ strong password policies or two-factor authentication.
As a result, attackers have a huge opportunity when it comes to small businesses – and it’s an opportunity that they usually take. Here are a few startling statistics as of 2021:
SMBs lost $212,000 in 2021 due to cyber incidents that affected suppliers with whom they share data.
At MicroTech, we’ve worked with hundreds of small businesses in Boise. We’ve seen cyber attacks take the same pattern time and time again. A trusting employee clicks on an untrustworthy link, a CEO accesses an account from an unsecured home computer, and consequences ensue.
To illustrate what happens, here’s a story from one of our customers (who was not a customer at the time of the phishing attempt) who very nearly destroyed her marketing business with a single click.
(Names Have Been Changed to Protect the Innocent)
We’re not here to embarrass anyone, and the point of our story is that this kind of cyber attack could happen to nearly everyone reading this – even you. Therefore, we’ve changed the name of our protagonist to Jenny Smith.
Jenny is the owner of a boutique marketing firm with ten full-time employees and a number of freelancers. They specialize in building marketing plans for institutions such as banks and hospitals. At the time of the cyber attack, they were above average in terms of their security preparations.
They were familiar with applicable compliance laws and used tools such as antivirus, firewalls, and security monitoring to defend themselves.
Jenny’s agency used Office 365 in the cloud for every aspect of their agency – email, word processing, document sharing, and more. This allowed their freelance users to access and add to their entire repository of documents while working from home. If a freelancer left the company or was hired, it was easy to provision and de-provision them. Meanwhile, much of their security was handled on the Microsoft platform – Jenny’s workers were mostly responsible for keeping their passwords secure.
Here’s where things got hairy.
Early on a Monday morning, Jenny was on a business trip. She received an email that looked like this:
.png?width=720&height=419&name=Phishing-Email-1-1-1024x597%20(1).png)
The email contained the Microsoft letterhead, used the Microsoft font, and contained a message that was certain to raise Jenny’s eyebrows – her payment for Microsoft Office had been declined. It conveniently included a login portal where Jenny could put in her correct payment information.
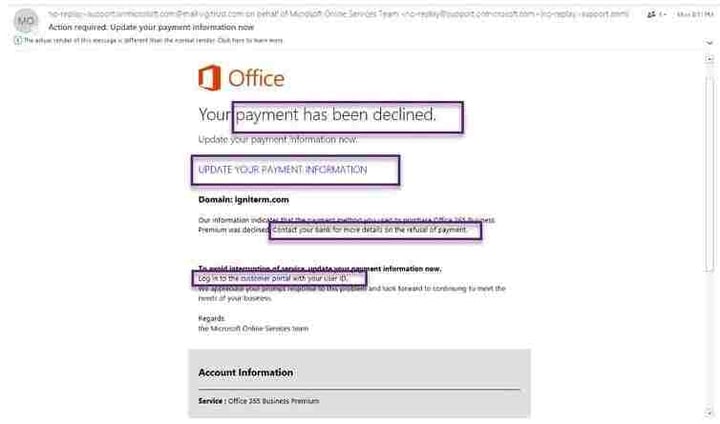
There’s only one suspicious item in the image – if you look carefully, the domain isn’t Microsoft.com – it’s “support.onmicrosoft.com.” Most people reading the domain name would see only what they expect to see.
Jenny was lucky. Instead of clicking on the email and putting in her login information, she thought that one of her credit cards had simply expired. Therefore, she simply forwarded the email to her bookkeeper asking to make sure that her Office 365 subscription be paid up. Then she forgot about it.
A week later, she received a different version of the same email. She was curious to see why the payment had not gone through.
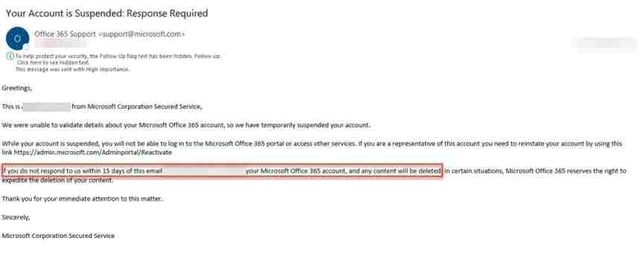
This time she clicked and logged in to what she thought was her Microsoft account.
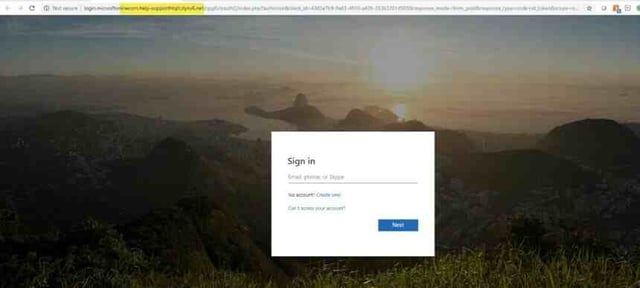
As soon as her browser rendered the page, she realized that something was off. Her URL read “electriccompany.microsoft.com,” not the ordinary Microsoft Office URL. She knew she’d been duped. The only question was, what would happen next?
Jenny was responsible about information security. She responded to the data breach by changing all her passwords right away. Nothing seemed to happen as a result of being hacked... At least not at first.
On Tuesday, five days after the incident, Jenny noticed that she could receive emails, but not send them. Since she needed to reply to up to 500 emails a week, this was a problem with a mission-critical application.
She put in a ticket with her hosting company, which called back. She spent two hours on the phone with a representative before being escalated to tier 2 support. They told her to wait until morning. Meanwhile, her clients were getting restless.
The next day was the same story – she could receive emails but not send them. After another three hours of troubleshooting with the hosting company, she was told to implement a double authenticity application from Microsoft. She does this.
At this point, Jenny has spent three days being unable to directly access her business email. Instead, she was replying to inquiries from her personal Gmail account, which left her clients confused. She spent five hours on the phone with support before being directed to Microsoft. After another two and a half hours, she received an answer
Jenny's email account was suspended after attackers stole her username and password and then used her account to send out 21,000 spam emails.
The next day came and Jenny did not receive a call back. Or the day after that. Or the day after that. In fact, Jenny didn’t receive a reply from Microsoft until a full 10 days after losing access to her account. On that day, after spending five hours on the phone with a technician, she was finally told that she needed to write a letter to the compliance board at Microsoft explaining the incident and asking to have her account reinstated.
Six days later, Jenny still wasn’t able to reply directly to emails, video conference with anyone, or schedule meetings efficiently. Her business was in freefall.
Finally, after calling Microsoft and begging for help, the company replied to her. It was now 22 days after losing her account. Although her account was reinstated, she was warned that one more compromise might result in her account being terminated for good.
In total, Jenny had to spend 17.5 hours on the phone over 22 days before she was able to regain access to the account.
In the meantime, her attacker had full access to her contact list, which could be vulnerable to further attacks. In the meantime, Jenny was still getting phishing emails – and if she or any of her employees clicked on one of them again, the whole nightmare would repeat itself.
Telling phishing emails and phishing sites apart from legitimate equivalents is a masterclass in noticing little details. The takeaway from this is that you will be fooled – there are no exceptions. What’s more, antivirus and firewalls can’t stop this kind of attack. Instead of planning to avoid phishing emails, plan to be attacked instead.
Working on their own, small businesses can help fight phishing attempts in three ways.
These methods are good, but they’re not foolproof – and they won’t help you mitigate the effects of an attack once it occurs.
If you want to avoid spending 22 days without access to email, work with a managed IT expert. They can help detect anomalies such as suspicious login attempts, multiple logins, or system failures – red flags that would have exposed Jenny’s attackers before they fully compromised her Office 365 account.
No business is ever safe from a cyber attack, but if you take the appropriate steps, you can save yourself from a lot of pain, hardship, and lost productivity. If you want to learn more, let's have a conversation.

Hackers are always looking for an opportunity to attack a company's devices and network. According to research, over 2,200 cyber-attacks happen daily, translating to one...

Sensitive information has become the lifeline of every modern business. Customer data, financial records, employee information, intellectual property, and operational...