
Small businesses underestimate cyber-attack protection believing in the false idea that cyber criminals only target large enterprises. In fact, the opposite is true.
It is not a matter of if you will be attacked, but when you will suffer a cyber attack, and if you will be able to prevent it and/or recover from it.
Research from the University of Maryland highlights that hackers launch attacks approximately every 39 seconds. With the proliferation of recent global attacks, it's evident that attackers are now more persistent, skilled, and better equipped than ever before. Previous warnings around the close of 2017 indicated an impending rise in cyber attacks, resulting in damages amounting to $5 billion. This signifies a significant increase by a factor of fifteen compared to just two years prior. Projections also pointed toward cybercrime-related losses reaching $6 trillion annually by 2021, accompanied by an estimated $1 trillion surge in cybersecurity spending over the ensuing four years.
Why are small businesses caught off guard? Because often they think, “We are a small business. Hackers only go after big businesses who can pay big dollars.” Not true!
The truth is that hackers don’t discriminate when it comes to their targets. They simply go after the easiest, most unsuspecting targets. Big businesses invest in expensive firewalls with professionally monitored intrusion protected systems. When they are attacked, they have both the IT expertise and manpower on board to find, prevent and/or mitigate attacks.
Conversely, small businesses are often caught off guard. Recent statistics indicate that 61% of small and medium-sized businesses (SMBs) encountered cyber attacks within the past year. Alarmingly, 54% of these breaches involved compromising customer and employee data.
Cyber-attacks can compromise an organization, no matter the size, at any given time. Traditional lines of defense such as firewalls and endpoint anti-virus won’t cut it against intelligent malware attacks. Advanced security measures today must go beyond traditional defenses. Many small companies follow the same basic design for their security needs – a pair of firewalls, arranged to create a DMZ, set around the perimeter of the organization. While this configuration can withstand casual attacks, dedicated ransomware and phishing attempts could circumvent these types of security measures entirely for two specific reasons:
In this blog, we will lay out what a layered security approach looks like specifically for small business, and what steps to take to ensure your employees are a part of the security solution and not a part of a security hack. Read on, this is a blog small business can not afford to miss.
Many security hacks and breaches are in fact non-technical. Phishing is often the result of fooling a well-intentioned employee into clicking on a link, providing information, resetting a password or even sending money from a source that they 'think' they know. A well-intentioned employee can be tricked into providing vital information without knowing that they are actually giving access to cybercriminals. Criminals use phishing tactics because it is usually easier to exploit your natural inclination to trust that it is to discover ways to hack into a well-protected system.
If you are in business and use email to do your job, chances are you receive phishing requests like the one shown in the next example. We had an employee who received an email from (what looked like) the Microsoft 365 team, asking her to confirm her account.
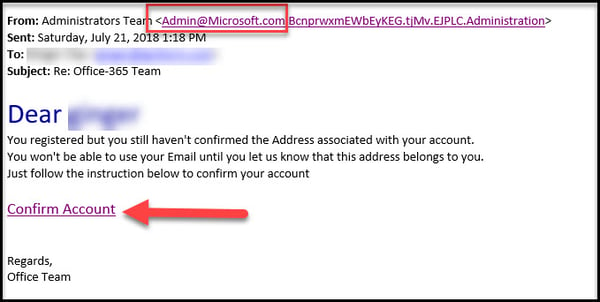
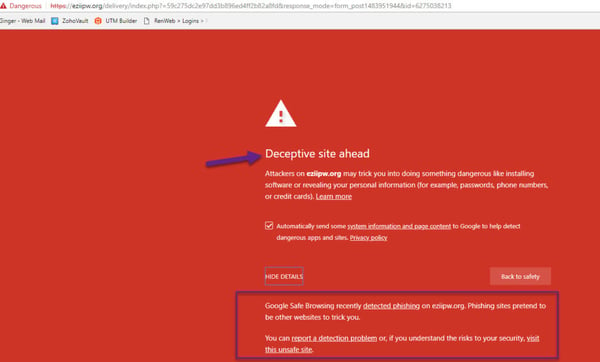
After extensive security employee awareness training and further investigation of this link, you will see that the link redirected to a non-Microsoft site that would have likely added malware to the network, or attempted to access sensitive network files.
Getting employees on-board with security prevention is the first and best way to protect your data. Here are some basic steps we recommend you consider:
Creating a culture of security awareness starts with training each and every employee to recognize the importance of security by being able to identify the signs of an impending threat.
Once you’ve created a culture of security awareness, the next step is to take proactive and preventive measures to secure your network. And while firewalls, anti-virus, and anti-malware software are basics in security protection, they don’t have the ability to proactively monitor, detect and decide how to remediate or recover stolen data or infected systems.
Here’s why it matters: Modern malware can hide deep in your computer without raising red flags. It will just quietly go about its business. And in fact, there are even “sneaky” viruses that will remove other viruses, so you don't get suspicious! Just because a virus isn't disruptive doesn't mean it isn't dangerous. It could be snagging your passwords, sensitive files or other vital information. And while endpoint detection and malware protection are table stakes for any businesses wanting to protect their business and customer data, monitored antivirus by a Managed IT expert is the only way to stay ahead of attacks.
They are able to monitor the network for irregularities that the non-expert would not have reason to suspect. Examples of this might include:
These types of reasons (and many more) lend themselves to the need for double-layer security expertise that a small business can typically not employee from within. IT experts have the ability to know which alerts to pay close attention to and how to spot unusual patterns. Continuous around the clock monitoring and “spot checking” by an outside expert provides the “eyes and ears” on the network that both prevent data breaches but also ensure you that your system is working at peak performance.
Small businesses need the same amount of help and protection against security threat as that of a medium or larger sized organization.
The long and short of the story is this: you need technology to innovate and be productive. Small businesses need it, even more, to “do more with less.” Technology has to be to be maintained for it to work the way you want it to work. Technology is constantly evolving and keeping up with hardware changes, software updates, patches and security protection can be a full-time job. Getting a handle on soaring IT costs can impact how you leverage that technology to be productive, service your clients and complete with other bigger businesses who can afford what a small business cannot. Managed IT is the means by which a small business pays a flat, monthly price for all IT services, upgrades, security, monitoring, and equipment updates. What has costs other businesses thousands to maintain is available to small business under a “managed IT” plan.
We’re not here to sell you anything. We are happy to talk you through your options.

Small businesses underestimate cyber-attack protection believing in the false idea that cyber criminals only target large enterprises. In fact, the opposite is true.

In today’s digital age, robust cybersecurity is essential for protecting businesses from increasing threats like data breaches, ransomware, and cyberattacks. Boise,...